Upgrading to MRENCLAVE Sealing
We are announcing an upgrade to version 1.18 that contains the following features:
- MRENCLAVE
- Transition to MRENCLAVE sealing
- Support for new governance proposal (upgrading from on MRENCLAVE to another)
- Support for Emergency Upgrade for the case the new enclave has a bug and is bricked
- By signatures of 66% of VP
- By signatures of M out of N validators in Emergency List (Currently 11 out of 25)
-
Setting hard-coded admin for certain contracts (by Shade request)
-
Added Code Hashes of SNIP contracts to the list of allowed code hashes
-
This will allow us to upgrade SNIP-2X contracts without breaking any existing contracts that may have the CodeHash hard coded
-
Updated tendermint.rs
Upgrade Procedure
The upgrade instructions are available here.
On Testnet, we also successfully tested the MRENCLAVE to MRENCLAVE upgrade and the Emergency Upgrade procedures.
The Emergency Upgrade procedure will also be tested on Mainnet post-upgrade (no network downtime will be involved)
MRSIGNER and MRENCLAVE - Into the Rabbit Hole
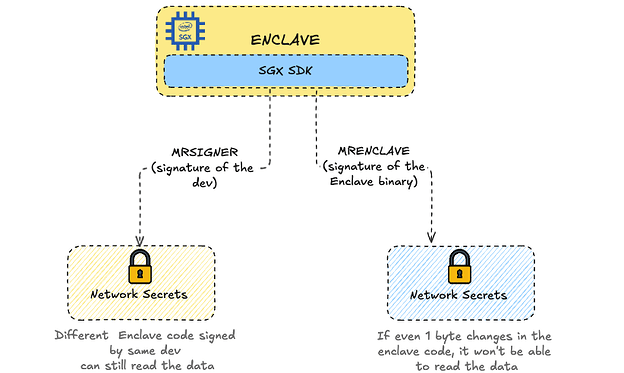
What are MRSIGNER and MRENCLAVE?
First, MR stands for “Measurement”, which can also be also understood as “Identity”. So, MRSIGNER and MRENCLAVE can be translated to plain language as “Signer Identity” and “Enclave Identity”.
In Intel SGX SDK, there are two ways to encrypt files:
- MRSIGNER - deriving the encryption key from the signature of the developer, and
- MRENCLAVE - deriving the encryption key from the contents of the actual Enclave binary that runs in the Intel SGX. In the case of Secret Network, the Enclave is the code that executes smart contracts .
In TEE lingo, file encryption is called sealing. In Secret, we use sealing to store critical information such as the network key on disk - this is required so that when a node restarts, it can read the network key on disk.
With MRSIGNER sealing, any code signed by the same developer can unseal the data.
Moving to MRENCLAVE makes sure that only the code that is explicitly approved by the community can ever get access to the secrets.
This makes the upgrade more complicated. With MRSIGNER, a new version of the Enclave can seamlessly read the network secrets encrypted by the previous version.
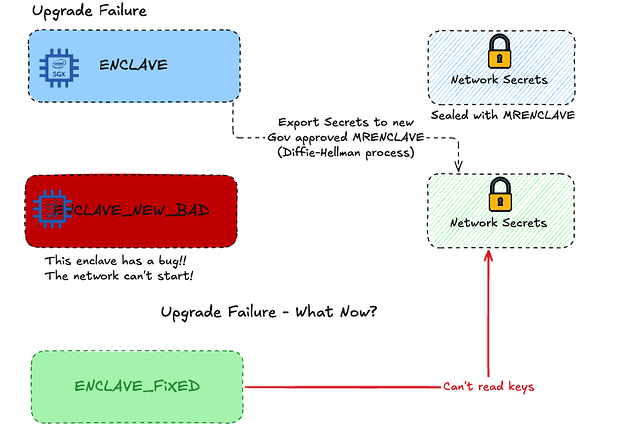
With MRENCLAVE, the keys need to be explicitly exported by the existing Enclave so that the new Enclave can read the network secrets and re-seal them with its MRENCLAVE.
This, however, introduces another potential risk. What happens if the new enclave has a critical bug and the network can’t start producing blocks?
With MRSIGNER sealing it was simple - we fix the bug and deploy the new code. But with MRENCLAVE sealing that wouldn’t work - the new enclave code would by definition have a different MRENCLAVE, and won’t be able to read the network secrets, and thus won’t be able to process transactions.
To mitigate this, we introduced the emergency upgrade procedures. If the new enclave has a critical bug and the network is down, we can create a new fixed enclave and instruct the “old” enclave to export the keys again so that the fixed enclave can take over.
The instruction to export keys to the new enclave has to be signed by the validators. There are two flavors of this signature:
- 66% of the voting power, or
- M out of N validators in a known list
The latter option is required for a very unlikely case when several validators with over 34% VP refuse or are unable to cooperate.
The emergency upgrade involves a manual process of validators signing a message that includes the “fixed” MRENCLAVE.
The message is then fed to the “old” node and it can export the keys and complete the upgrade
In this release, the M out of N is set to be 11 out of 25 hard-coded validators. The list of validators is available here. When creating the list, we wanted to make it diverse, including Secret OGs, institutions and projects, making it unlikely that there is a possibility of collusion.
The list can be updated from time to time as needed.
Conclusion
MRENCLAVE upgrade makes Secret Network more secure and resilient, making sure that only the approved code can access the network secrets.
Later this year, we will complete the process by going through key rotation procedure, changing the network seed for Secret Network.